Cyber breaches have increased from 2020 to 2021 by 31%. In 2025, the cost of cybercrime will be $10 trillion, affecting businesses, governments, and individuals. Your online activity and sensitive data are increasingly high-risk targets for criminals too.


SOCKS5 proxy is suitable for private traffic network routing. But it is not as secure as HTTPS proxies or VPNs. However, it is versatile and compatible with several networking protocols like SMTP and FTP. In short, it can handle many tasks like email forwarding and file transfers with faster performance.
The article unpacks the SOCKS5 proxy, the protocols it supports, and its applications. Now, let’s dive in, shall we?
What is SOCKS5 Proxy?
SOCKS refers to Socket Secure, an internet security protocol that enhances online privacy and data integrity. A SOCKS proxy is typically used to route traffic through a firewall on behalf of a client.
SOCKS data transfer protocol has evolved from SOCKS, SOCKS4, and now SOCKS5. The difference between the current and old versions is the types of connections supported. SOCKS4 only supports transmission control protocol (TCP) connections.
On the other hand, SOCKS5 supports more connections and protocols, which is the article’s main focus. The several protocols supported by SOCKS5 make it a versatile proxy for wide applications. Besides, it has enhanced security features through its key authentication methods:
- Authentication using username and password to connect to the SOCKS5 proxy.
- Null authentication that does not require authentication to connect to the proxy.
- GSS-API authentication involves both you (client) and the server confirming your identity before connection.
Benefits of SOCKS5 Proxy



A. Paid and Free Proxy Servers are Available
There are both paid and free SOCKS5 proxy servers. SOCKS 5 has reserved port 1080 for proxy servers. You can still forward emails, transfer files, and download or upload files privately and anonymously, even if you’re on a budget. There is a list of free proxy you can use for your needs.
However, free proxies can easily leak your details and have unreliable connections. Paid SOCKS5 proxies may make the experience less painful. Several proxy providers offer high-performance proxies that you can choose depending on your needs and targets.
B. By-Pass IP Bans
SOCKS5 proxy can help you bypass firewalls or IP bans. So, it can come in handy if your virtual private network (VPNs) or original IP is blocked by a website. You can use it to reroute your traffic and bypass the block.
However, it is difficult to bypass national firewalls using SOCKS5 proxies. National firewalls use deep packet inspection (DPI) restricting your access by ISPs on blacklisted websites. Only VPNs can easily handle such national firewalls.
C. Reliable With High Speed
SOCKS5 proxy can work with user datagram protocol (UDP) and TCP amongst other protocols. The previous versions only supported TCP connections. For TCP connections, all packets are received from the client or server and formatted for easy transmission.
That is different from UDP. In UDP connections, packets are sent as received and are not formatted for transmission. Hence, they are not necessarily transmitted in sequential order and that saves time. Overall, it reduces time wastage that boosts SOCKS5 proxy speed and connection reliability.
D. Better Performance
On top of speed, SOCKS5 proxies have performance as part of the package. It is common for many proxies to rewrite data packet headers for traffic re-routing. However, the rewrites are prone to errors that can lead to misrouting of data.
For SOCKS5 proxy servers, there is no labeling or rewriting of data packet headers. As a result, it incredibly reduces its errors that improve its performance. Unfortunately, it makes it easy to read packet headers that contain sensitive and personal information. So, the performance comes at security and privacy costs.
Types of Protocol for SOCKS5 Proxy
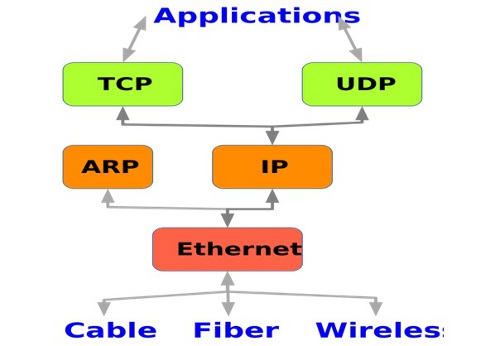


1. TCP (Transmission Control Protocol)
The transmission control protocol is an Internet protocol that ensures effective data transfers between applications and devices. For SOCKS5 proxy servers, TCP connections help to route data past firewalls or IP blocks.
TCP breaks messages or requests into data packets that are transmitted independently. When the packets reach the client or server, they are reconstituted into the original request. Besides, different request formats are reformatted for easy and faster transmission.
The proxy server uses port 1080 to receive the client’s incoming traffic. And it can reroute it without using the original IP address on the data packet headers. The TCP connections make it possible to bypass internet blocks.
2. UDP (User Datagram Protocol)
The user datagram protocol (UDP) sends messages (datagram) to hosts on the internet. UDP only offers data integrity through checksum to evaluate for data bits modification. In other words, it checks if your requests or data has been altered in any way.
It also depends on port numbers for the source and destination of messages. But, it is very unreliable since it does not offer sequential data packet ordering, delivery assurance, or duplication guarantee.
However, depending on your use case and application, you can still achieve error-correction techniques. The correction techniques are possible on the TCP or SCTP (stream control transmission protocols).
The best part of UDP is that it saves time. Without ordering data packets or reformatting them, UDP is suitable for real-time applications. So, SOCKS5 proxies on UDP connections are very fast.
3. SSH (Secure Shell)
Secure Shell (SSH) protocol provides secure network services devoid of overhearing and tampering. It assures services in even an unsecured network based on a client-server architecture.
SSH has several suites for different applications. One of the suites is the OpenSSH which facilitates dynamic port forwarding enabling you to create a local SOCKS proxy. So, it can expand your connections beyond just a remote port and server.
The SSH protocol makes the SOCKS5 proxy act like a VPN by forwarding connections. Major secure applications like Tor use SOCKS interfaces for their clients (users). So, SOCKS5 proxy servers’ underlying protocols make it versatile and effective in its functions.
Takeaway
There has never been a better moment to enhance online security and privacy. With increasing cyber threats, proxy servers are one of the ways of ensuring your personal data is safe and remains private.
SOCKS5 proxies provide a versatility and robust performance package for your online needs. It uses protocols like TCP, UDP, and SSH allowing it to offer wide applications as you need.
Besides, using UDP connections can offer faster speeds best suitable for real-time applications. If you wish to bypass IP bans and speed is a deal-breaker, then SOCKS5 proxies are the partner you need.