External penetration testing is a type of external security assessment. It is useful as a way to test the external protections of an organization. External penetration tests are often conducted as part of a risk management program. This blog post will answer some of the common questions about external penetration tests so you know what is appropriate for your company!
External Penetration Testing vs Vulnerability Assessment
Both vulnerability scanning and external penetration testing can help organizations find exploitable vulnerabilities in their external defenses. However, they’re actually two different concepts altogether.
External and internal vulnerability scanning can provide valuable information about the security of your IT infrastructure. However, unlike external penetrative testing, they do not actually test the external protections of an organization. This means that a penetration test exploits the weaknesses and analysis them. On the other hand, a vulnerability assessment merely lists them out.
External Penetration Testing vs Internal Penetration Testing
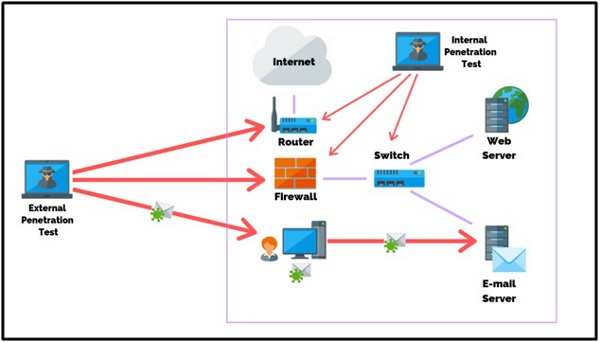


In simple words, we conduct external penetration tests on external protections, whereas internal penetration tests focus on weaknesses in network security internally. However, these types of assessments are not mutually exclusive; an external pen test can include some elements of an internal one to more comprehensively assess your company’s external protections.
When Should You Conduct External Penetration Testing
External penetration testing often requires the assistance of an external consultancy. You have to perform external penetration tests when your company conducts a full risk assessment. Risk assessments usually occur in the early stages of an organization’s life cycle. However, you can also use them to supplement any type of security audit later on depending on your company’s specific needs and requirements. A penetration test is really part of a larger external security review.
When to conduct external penetration testing depends on several factors such as your company’s business sector and services provided. For example, if you work in financial services you would definitely want to perform external penetration testing, but if you work in a less sensitive industry external penetration tests may not be necessary.
What Are The Steps Involved In Conducting External Penetration Testing?
Organizations should first decide how they want to perform the external penetration tests (on-site, remote) and who will conduct them. Organizations then need to identify external protections that can be tested for vulnerabilities. This process often involves identifying external firewalls, IDS/IPS devices, routers, wireless access points (WAPs), web proxies, or other external protections an organization may have in place. Finally, testers perform pen tests against external protections to find vulnerabilities.
After this initial identification of external devices is complete, the actual testing begins with a vulnerability scan on each device to determine if any known exploits could lead to security breaches. Once all possible vulnerabilities are documented by the pen testers, they begin their assessment of those flaws. Finally, they report back both positive and negative findings in a detailed report so your company can make necessary changes to external protections.
How Do External Penetration Testing Reports Work?
Testers document the external penetration test results in a report that you will receive after the tests. The external penetration test report should include vulnerabilities found, risk levels of those vulnerabilities, and recommendations for addressing or remediating these issues.
What Are The Costs Involved In External Penetration Testing?
The cost of external pen tests depends on how many external devices need to be tested and if they’re being done remotely or on-site. Organizations should expect costs ranging from a few thousand dollars for basic external protection testing up to tens of thousands of dollars when more complex situations arise that require additional testing time, specific expertise, etc.
How External Penetration Testing Is Evolving Beyond The Basics?
The external pen test process has evolved to address new technologies and emerging threats, such as advanced persistent threats (APTs). As a result, progress in external protection systems, traditional external pen tests are no longer enough; they need significant adjustments for modern-day usage.
- These include increasing awareness about endpoint security within your company’s infrastructure because it provides more insight into protecting data on workstations that attackers would target first when trying to gain access to an organization’s network.
- Organizations should consider focusing their attention on securing cloud services hosting critical data because attacks often begin with compromised public-facing websites or social media accounts before moving inward towards protected resources like databases and other sensitive information assets hidden behind
What Questions Should I Ask During External Penetration Tests?
During pentest, you have to involve yourself in the process by asking many questions, like:
- How will the organization conduct external penetration testing (on-site versus remote)?
- Who will perform the external penetration tests?
- Is it possible to record and track all communications between testers and company employees? If so, how is this accomplished?
Conclusion
If you want to really enhance your business security, you need to test your application’s security externally too! Testers from an outside firm and has no prior knowledge of any vulnerabilities in its infrastructure usually conduct the external penetration tests. We hope this post answers any questions you had about external penetration testing.